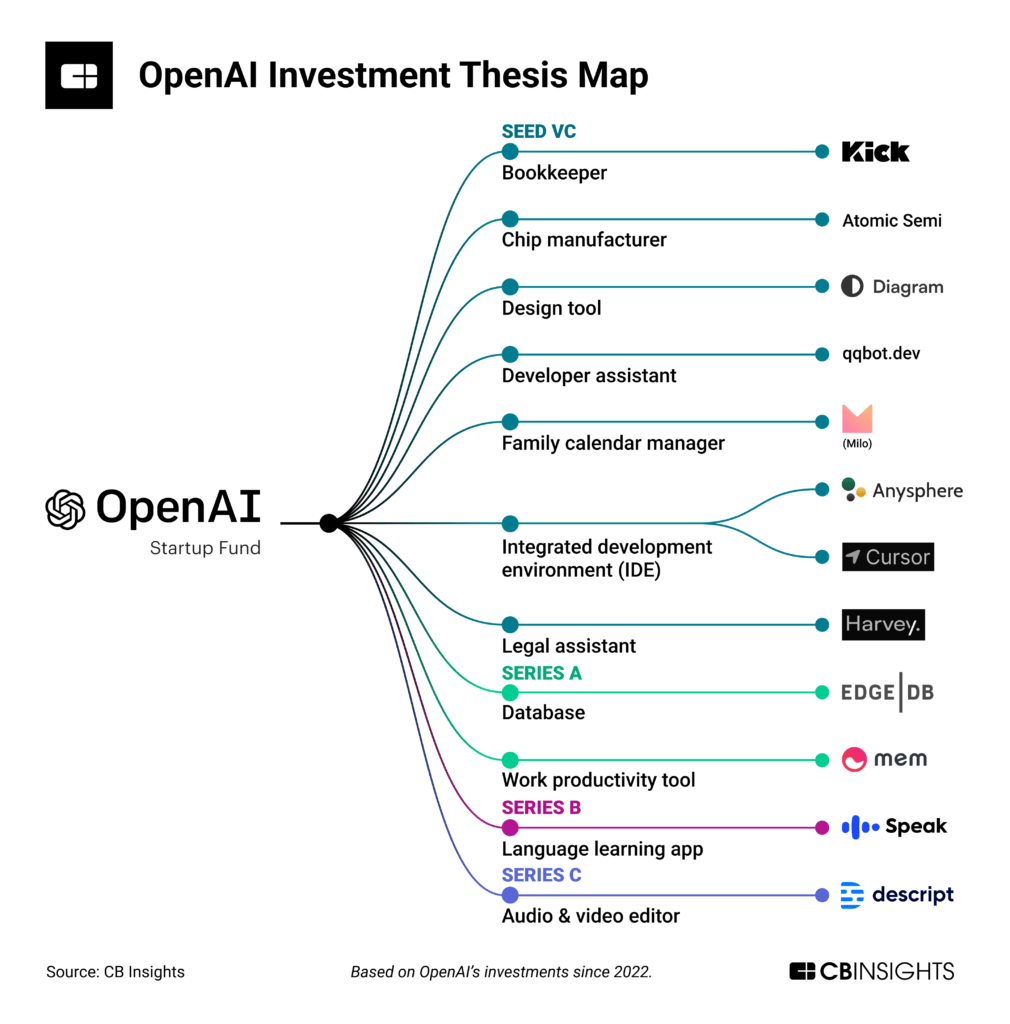
The Internet of Things (IoT) has become an integral part of modern life, connecting billions of devices and transforming industries across the globe. As IoT continues to grow and evolve, understanding the engineering aspects of this technology becomes increasingly important. This article delves into the various components of the Internet of Things systems, including architecture, protocols, security, device design and development, and system integration. By exploring these elements in detail, you will gain a deeper understanding of the technical foundations of the Internet of Things and how they contribute to the successful implementation and management of IoT systems.
1. IoT Architecture
1.1. IoT Devices and Sensors
IoT sensors and devices play a crucial role in the Internet of Things ecosystem, as they are responsible for collecting data from the physical environment and converting it into digital signals. These devices can range from simple temperature sensors to complex industrial machinery equipped with multiple sensors. The choice of sensors depends on the specific application and the type of data required.
Several types of sensors are commonly used in the IoT platform, including temperature, humidity, pressure, motion, and light sensors. For example, temperature sensors are widely used in smart home applications to monitor and control heating and cooling systems. Humidity sensors can be found in agricultural IoT systems to optimize irrigation and maintain optimal growing conditions for crops. Pressure sensors are often used in industrial settings to monitor fluid levels and detect leaks in pipelines.
In addition to these common sensor types, IoT devices can also incorporate more specialized internet-connected sensors, such as gas sensors for air quality monitoring, accelerometers for tracking movement, and GPS modules for location tracking. These sensors enable IoT devices to gather a wide range of data, providing valuable insights and enabling more efficient and intelligent decision-making across various industries.
Further Reading: Driving Innovation: Harnessing IoT Potential in the Automotive Sector
1.2. IoT Connectivity
IoT devices rely on various connectivity options to transmit data between sensors, actuators, and other components within the IoT ecosystem. The choice of connectivity depends on factors such as range, power consumption, data rate, and cost. Some of the most common IoT connectivity options include Wi-Fi, Bluetooth, and cellular networks.
Wi-Fi
Wi-Fi is a widely used connectivity option for IoT devices, especially in indoor environments. It offers high data rates, typically up to 600 Mbps for Wi-Fi 4 (802.11n) and 9.6 Gbps for Wi-Fi 6 (802.11ax). Wi-Fi operates in the 2.4 GHz and 5 GHz frequency bands, providing a range of up to 100 meters indoors. However, Wi-Fi’s power consumption can be relatively high, making it less suitable for battery-powered devices.
Bluetooth
Bluetooth is another popular IoT connectivity option, particularly for short-range, low-power applications. Bluetooth Low Energy (BLE), introduced in Bluetooth 4.0, is specifically designed for IoT devices, offering low power consumption and data rates up to 2 Mbps. BLE operates in the 2.4 GHz frequency band and has a range of up to 100 meters, depending on the environment and device configuration.
Cellular Networks
Cellular networks provide IoT connectivity over long distances, making them ideal for applications such as asset tracking and remote monitoring. Cellular IoT technologies include Narrowband IoT (NB-IoT) and LTE-M. NB-IoT operates in the licensed spectrum, offering a range of up to 10 km and data rates of up to 250 kbps. LTE-M, on the other hand, provides higher data rates (up to 1 Mbps) and supports voice communication. Both NB-IoT and LTE-M are designed for low-power operation, enabling extended battery life for IoT devices.
In addition to these common connectivity options, other wireless technologies such as LoRaWAN, Sigfox, and Zigbee are also used in IoT applications, each with its own set of advantages and trade-offs. Ultimately, the choice of IoT connectivity depends on the specific requirements of the application, including factors such as range, data rate, power consumption, and cost.
Further Reading: About Wireless IoT Architecture
1.3. IoT Data Processing and Storage
Data processing and storage are critical components of IoT systems, as they enable the transformation of raw sensor data into actionable insights. With the vast amount of data generated by IoT devices, efficient data processing, and storage solutions are essential for managing and analyzing this information. In this regard, the following two options are the best IoT data processing and storage.
Cloud Computing
Cloud computing plays a significant role in IoT data management, as it provides scalable and flexible storage and processing capabilities. Cloud-based platforms, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform, offer various services tailored to IoT data processing and storage needs. These platforms enable the collection, storage, and analysis of data from IoT devices, often providing real-time processing capabilities and advanced analytics tools.
However, relying solely on cloud computing for data processing and storage can introduce latency and bandwidth issues, especially in scenarios where real-time decision-making is crucial. To address these challenges, edge computing has emerged as an alternative or complementary approach to cloud computing.
Edge Computing
Edge computing involves processing data closer to the source, i.e., on the IoT devices themselves or on nearby edge servers. This approach reduces the need to transmit data to the cloud, minimizing latency and bandwidth requirements.
Edge computing can be particularly beneficial in applications where real-time processing is critical, such as autonomous vehicles, industrial automation, and smart city infrastructure. These systems can make faster decisions and respond more effectively to changing conditions by processing data at the edge.
Choosing the right combination of cloud and edge computing depends on the specific requirements of the IoT application, such as latency, bandwidth, and real-time processing needs.
1.4. IoT Applications and Services
IoT applications and services are responsible for delivering value to end-users by leveraging the data collected and processed by IoT devices. These applications and services can be found across various industries, addressing a wide range of challenges and opportunities. Some common areas of application are discussed below.
Smart Homes
Smart homes are a prominent example of IoT applications, where devices such as smart thermostats, lighting systems, and security cameras work together to create a more comfortable, energy-efficient, and secure living environment. By analyzing data from sensors and user preferences, smart home systems can automatically adjust temperature, lighting, and other settings to optimize energy consumption and enhance the user experience.
Industrial IoT (IIoT)
Industrial IoT (IIoT) is another significant area of IoT applications, focusing on improving efficiency, productivity, and safety in manufacturing and other industrial sectors. IIoT systems can monitor equipment performance, figure out predictive maintenance needs, and optimize production processes using data from sensors and advanced analytics. For example, an IIoT system might use vibration sensors on a production line to detect early signs of equipment failure, allowing for proactive maintenance and reducing downtime.
Agriculture
Agriculture is another industry that has embraced the benefits of IoT technology, with applications such as precision farming and livestock monitoring. IoT devices can collect data on soil moisture, temperature, and nutrient levels, enabling farmers to optimize irrigation and fertilization strategies. Livestock monitoring systems can track the health and location of animals, helping farmers to improve animal welfare and productivity.
Smart Cities
Smart cities leverage IoT technology to enhance urban infrastructure and services, such as traffic management, waste management, and public safety. For instance, IoT-enabled traffic lights can adapt to real-time traffic conditions, reducing congestion and improving traffic flow. Similarly, smart waste management systems can optimize collection routes based on sensor data from waste containers, reducing fuel consumption and emissions.
Further Reading: Smart City Internet of Things: Revolutionising Urban Living
These examples represent just a few of the many IoT applications and services that are transforming industries and improving our daily lives. By harnessing the power of IoT data, these applications enable more efficient, sustainable, and intelligent decision-making, ultimately delivering value to end-users and society as a whole.
2. IoT Protocols
2.1. MQTT
MQTT (Message Queuing Telemetry Transport) is a lightweight messaging protocol designed for IoT systems, particularly in scenarios where low bandwidth, high latency, or unreliable networks are present. MQTT operates on a publish-subscribe model, which allows devices to send messages (publish) to a central broker, which then distributes the messages to other devices (subscribers) interested in the specific topic.
One of the main advantages of MQTT is its low overhead, as it uses a compact binary format for message encoding, reducing the amount of data transmitted over the network. This makes it well-suited for resource-constrained IoT devices and networks with limited bandwidth. Additionally, MQTT supports Quality of Service (QoS) levels, allowing developers to choose between different message delivery guarantees based on the requirements of their IoT application.
A common use case for MQTT is in smart home systems, where various IoT devices, such as sensors, actuators, and controllers, need to communicate with each other and a central hub. For example, a temperature sensor might publish its readings to an MQTT broker, which then forwards the data to a smart thermostat subscribed to the temperature topic. The thermostat can then adjust the heating or cooling system accordingly based on the received data.
2.2. CoAP
The Constrained Application Protocol (CoAP) is a lightweight IoT protocol designed for resource-constrained devices and low-power networks. CoAP is built on top of the User Datagram Protocol (UDP) and provides a simple yet efficient communication mechanism for IoT devices. Its primary purpose is to enable machine-to-machine (M2M) communication in environments where low power consumption, low latency, and small message sizes are critical.
One of the key advantages of CoAP is its low overhead, which makes it suitable for devices with limited processing power and memory. CoAP messages are typically smaller than those used in other IoT protocols, such as HTTP, reducing the amount of data that needs to be transmitted and processed. This reduced overhead leads to lower power consumption and faster communication, which are essential for battery-powered IoT devices.
CoAP also supports a request-response communication model, similar to HTTP, allowing devices to exchange data in a familiar and straightforward manner. However, unlike HTTP, CoAP is designed to operate over unreliable networks, incorporating features such as message retransmission and duplicate detection to ensure reliable communication.
Another notable feature of CoAP is its support for the observed pattern, which enables devices to subscribe to resources and receive notifications when the resource state changes. This feature allows IoT devices to efficiently monitor and react to changes in their environment without the need for constant polling.
2.3. Zigbee
Zigbee is a wireless communication protocol designed for low-power, low-data-rate IoT applications, such as home automation, industrial automation, and smart energy management. Zigbee operates in the 2.4 GHz frequency band, offering data rates up to 250 kbps and a range of up to 100 meters, depending on the environment and device configuration.
One of the key features of Zigbee is its support for mesh networking, which allows devices to communicate with each other directly or through intermediate nodes, extending the overall network range and improving reliability. In a Zigbee mesh network, devices can act as routers, relaying messages between other devices and the network coordinator. This self-healing and self-organizing capability makes Zigbee networks highly robust and adaptable to changing conditions.
Zigbee’s low power consumption makes it an attractive option for battery-powered IoT devices, such as sensors and actuators. Additionally, Zigbee provides built-in security features, including encryption and authentication, to protect data and ensure the integrity of the network.
A common use case for Zigbee is in smart lighting systems, where multiple light bulbs, switches, and sensors can form a mesh network to communicate with each other and a central hub. This enables advanced lighting control features like dimming, color changing, and scheduling while maintaining low power consumption and a reliable network connection.
3. IoT Security
3.1. Security Challenges in IoT
IoT systems face unique security challenges due to their distributed nature, the large number of connected devices, and diverse communication protocols and standards. Addressing these challenges is essential to ensure the privacy, integrity, and availability of IoT systems and the data they generate.
Here are some common security challenges in IoT.
Large Surface Attack
One of the primary security challenges in IoT is the large attack surface created by the sheer number of connected devices. With billions of IoT devices deployed worldwide, attackers have numerous potential entry points to compromise networks and gain unauthorized access to sensitive data. Furthermore, many IoT devices have limited processing power and memory, making it difficult to implement robust security measures.
Insecure Communication
Insecure communication between IoT devices and other components of the system is another significant security challenge. IoT devices often transmit data over wireless networks, which can be susceptible to eavesdropping, interception, and tampering. Ensuring secure communication requires the implementation of encryption and authentication mechanisms, which can be challenging for resource-constrained devices.
Device and Firmware Vulnerabilities
Device and firmware vulnerabilities also pose security risks in IoT systems. Many IoT devices run on outdated or poorly maintained firmware, which can contain security vulnerabilities that attackers can exploit. Ensuring that devices are regularly updated with the latest security patches is crucial to mitigate these risks.
Lack of Standardization
Lack of standardization in IoT security is another challenge, as there is no universally accepted set of security guidelines or best practices for IoT systems. This can lead to inconsistent security measures across devices and networks, making it difficult to ensure comprehensive protection.
Addressing these challenges is essential to ensure the privacy, integrity, and availability of IoT systems and the data they generate.
Further Reading: The challenges of IoT security
3.2. IoT Security Best Practices
Ensuring the security of IoT systems is crucial to protect sensitive data, maintain user privacy, and prevent unauthorized access or control of devices. Implementing security best practices can help mitigate risks and safeguard IoT systems from potential threats.
Some of these best practices include:
Device hardening
Strengthening the security of IoT devices involves minimizing potential attack surfaces and vulnerabilities. This can be achieved by disabling unnecessary services, closing open ports, and removing default credentials. Regularly updating firmware and software to patch known vulnerabilities is also essential for maintaining device security.
Secure communication
IoT devices should use encrypted communication channels to protect data from eavesdropping and tampering. Protocols such as TLS (Transport Layer Security) can be used to share data securely between devices and servers. Additionally, implementing secure key management practices, such as using unique cryptographic keys for each device, can further enhance communication security.
Data protection
Ensuring the confidentiality, integrity, and availability of data is a critical aspect of IoT security. This involves encrypting sensitive data both at rest and in transit, implementing access controls to restrict unauthorized access to data, and regularly backing up data to prevent loss in case of system failures or security incidents.
Network segmentation
Separating IoT devices into different network segments can help limit the potential impact of a security breach. An attacker’s ability to move laterally within the network is hindered by isolating devices and restricting communication between segments. This can be achieved using techniques such as virtual LANs (VLANs) or network firewalls.
Monitoring and incident response
Continuously monitoring IoT systems for signs of suspicious activity or potential security incidents is crucial for early detection and response. Implementing intrusion detection systems (IDS) and security information and event management (SIEM) solutions can help identify and alert potential threats. Establishing a well-defined incident response plan can ensure timely and effective action in case of a security breach.
By following these IoT security best practices, organizations can significantly reduce the risk of security incidents and protect their IoT systems from potential threats. Implementing a comprehensive security strategy that addresses device, communication, data, and network security is essential for maintaining the trust and confidence of users and stakeholders in IoT systems.
Further Reading: Red Team Vs. Blue Team: An In-depth Analysis of Cybersecurity Operations
3.3. IoT Security Standards and Frameworks
Security standards and frameworks play a vital role in guiding organizations to implement effective security measures for IoT systems. These standards and frameworks provide best practices, guidelines, and recommendations for securing IoT devices, communication, data, and networks. Some widely-adopted IoT security standards and frameworks include:
ISO/IEC 27001
This international standard specifies the requirements for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). ISO/IEC 27001 systematically manages sensitive information and ensures its confidentiality, integrity, and availability. While not specific to IoT, this standard can be applied to IoT systems to ensure a comprehensive and risk-based approach to information security.
NIST Cybersecurity Framework
Developed by the US National Institute of Standards and Technology (NIST), this voluntary framework provides guidelines for organizations to manage and reduce cybersecurity risks. The NIST Cybersecurity Framework consists of five core functions: Identify, Protect, Detect, Respond, and Recover. These functions can be applied to IoT systems to help organizations assess and improve their cybersecurity posture.
IIC Industrial Internet Security Framework (IISF)
The Industrial Internet Consortium (IIC) developed the IISF to address the unique security challenges of Industrial IoT (IIoT) systems. The IISF provides a comprehensive set of guidelines and best practices for securing IIoT systems, covering aspects such as device security, data protection, and network security. The IISF is designed to be applicable across various industries and can be tailored to specific IIoT use cases.
ETSI EN 303 645
This standard, developed by the European Telecommunications Standards Institute (ETSI), focuses on the cybersecurity of consumer IoT devices. ETSI EN 303 645 provides a set of 13 provisions that cover various aspects of IoT security, such as secure software development, data protection, and secure communication. The standard aims to help manufacturers and developers build secure IoT devices and protect consumer privacy.
By following the guidelines and best practices provided by these standards, organizations can mitigate security risks and protect their IoT devices, data, and networks from potential threats.
4. IoT Device Design and Development
4.1. Hardware Design Considerations
When designing IoT devices, several hardware design considerations must be taken into account to ensure optimal performance, reliability, and security. These considerations include power consumption, form factor, and connectivity options.
Power Consumption
Power consumption is critical in IoT device design, particularly for battery-powered devices. Designers must balance the need for processing power, memory, and communication capabilities with the constraints imposed by limited energy resources. Techniques for reducing power consumption include using low-power components, optimizing firmware and software for energy efficiency, and implementing power management strategies, such as duty cycling and sleep modes.
Form Factor
The form factor is another important consideration, as IoT devices often need to be small and unobtrusive to fit seamlessly into their intended environments. Designers must carefully select components and layout designs that minimize the device’s size and weight while maintaining the required functionality. This may involve using miniaturized components, such as microcontrollers, sensors, and antennas, as well as employing innovative packaging and assembly techniques.
Connectivity Options
Connectivity options play a crucial role in IoT device design, as they determine how the device communicates with other components in the IoT ecosystem. Designers must choose the appropriate connectivity technology based on factors such as range, data rate, power consumption, and cost. As discussed earlier, common IoT connectivity options include Wi-Fi, Bluetooth, cellular networks, and other wireless technologies like Zigbee, LoRaWAN, and Sigfox.
4.2. IoT Firmware and Software Development
IoT firmware and software development is a critical aspect of IoT device design, with a focus on optimizing for resource constraints, ensuring security and privacy, promoting modularity and scalability, enabling interoperability and standardization, and conducting thorough testing and validation. Let’s discuss them one by one.
Optimizing for resource constraints
IoT devices often have limited processing power, memory, and energy resources. As a result, firmware and software must be optimized to minimize resource consumption while maintaining the required functionality. This can involve using efficient algorithms, minimizing memory usage, and implementing power-saving techniques, such as duty cycling and sleep modes.
Security and privacy
Ensuring the security and privacy of IoT devices is crucial to protect sensitive data and prevent unauthorized access or control. Firmware and software developers must implement security best practices, such as secure boot, encryption, and authentication, to safeguard devices and data. Regularly updating firmware and software to patch known vulnerabilities is also essential for maintaining device security.
Modularity and scalability
Designing firmware and software with modularity and scalability in mind can facilitate the integration of new features, updates, and improvements. This can be achieved by using a modular architecture, which allows individual components to be updated or replaced without affecting the entire system. Scalability is also important, as IoT systems may need to accommodate a growing number of devices and increased data processing requirements over time.
Interoperability and standardization
IoT devices often need to communicate with other devices and systems, which may use different communication protocols and data formats. Ensuring interoperability between devices and systems requires the use of standardized protocols and data formats, as well as the implementation of translation and adaptation mechanisms when necessary.
Testing and validation
Rigorous testing and validation of firmware and software are essential to ensure the reliability and security of IoT devices. This includes functional testing to verify that the device performs as expected and security testing to identify and address potential vulnerabilities. Automated testing tools and frameworks can help streamline the testing process and ensure comprehensive coverage of potential issues.
By adhering to these principles, developers can create robust, secure, and efficient IoT devices that meet the diverse requirements of various IoT applications.
4.3. IoT Device Testing and Validation
Testing and validation are essential steps in the development of IoT devices, ensuring that they meet performance, reliability, and security requirements. Rigorous testing helps identify and address potential issues before devices are deployed in real-world environments, reducing the risk of failures and security incidents.
Functional Testing
Functional testing verifies that the IoT device performs as expected, according to its design specifications. This involves testing individual components, such as sensors, actuators, and communication modules, as well as the overall system functionality. Functional testing can include input validation, output verification, and testing of various use cases and scenarios.
Performance Testing
Performance testing evaluates the IoT device’s ability to handle specific workloads and operating conditions, such as high data rates, large numbers of connected devices, or extreme temperatures. Performance testing can help identify bottlenecks and limitations in the device’s hardware and software, enabling developers to optimize the system for maximum efficiency and reliability.
Security Testing
Security testing is crucial for identifying and addressing potential vulnerabilities in IoT devices. This can involve penetration testing, where security experts attempt to exploit vulnerabilities to gain unauthorized access to the device or its data. Security testing can also include static and dynamic analysis of the device’s firmware and software and evaluation of encryption and authentication mechanisms.
Environmental Testing
Environmental testing assesses the IoT device’s ability to operate under various environmental conditions, such as temperature, humidity, and vibration. This type of testing is particularly important for devices deployed in harsh or unpredictable environments, such as industrial settings or outdoor locations.
Interoperability testing
Interoperability testing ensures that the IoT device can communicate and interact with other devices and systems in the IoT ecosystem. This involves testing the device’s compatibility with various communication protocols, standards, and platforms and its ability to function within a heterogeneous network of devices.
By conducting thorough testing across various dimensions, developers can identify and address potential issues before devices are deployed, ultimately resulting in more reliable and secure IoT systems.
Further Reading: Red Teaming Vs. Pen Testing- understanding the distinctive nature and Purpose of cybersecurity tactics
5. IoT System Integration
5.1. IoT Device Management
Managing IoT devices is a complex task involving handling various aspects such as device provisioning, monitoring, and updates. Addressing these challenges is essential for maintaining the performance, security, and reliability of IoT systems.
Device provisioning
Device provisioning is the process of adding new devices to the IoT system and configuring them with the necessary settings, such as network parameters, security credentials, and application-specific configurations. This process can be automated using device management platforms to streamline the provisioning process and ensure consistent configurations across all devices.
Monitoring
Monitoring is essential for maintaining the health and performance of IoT devices. This involves collecting and analyzing data from devices, such as sensor readings, device status, and performance metrics. Monitoring can help identify potential issues, such as hardware failures, connectivity problems, or security incidents, allowing for proactive maintenance and remediation.
Updates
Updates are crucial for keeping IoT devices secure and up-to-date with the latest features and improvements. This includes firmware updates, which can patch security vulnerabilities and enhance device functionality, as well as software updates for applications and services running on the devices. Implementing a robust update mechanism is essential for ensuring that devices receive timely updates and minimizing the risk of security incidents.
By addressing these challenges, organizations can maintain their IoT solutions’ performance, security, and reliability, ensuring that physical devices operate effectively and deliver value to end-users.
Further Reading: What is IoT device management
5.2. IoT Data Integration
Integrating IoT data with other systems and applications is essential for maximizing the value of IoT deployments. By combining IoT data with data from other sources, organizations can gain deeper insights, make more informed decisions, and optimize their operations. However, data integration can present several challenges, which must be addressed to ensure seamless and efficient data flow between IoT devices and other systems.
Data format and protocol compatibility
IoT devices often generate data in various formats and use different communication protocols, which can create compatibility issues when integrating data with other systems. To address this challenge, developers can implement data translation and adaptation mechanisms, such as middleware or data integration platforms, which can convert data between different formats and protocols.
Data quality and consistency
Ensuring the quality and consistency of IoT data is crucial for accurate analysis and decision-making. Data quality issues, such as missing, duplicate, or erroneous data, can arise from various sources, including sensor malfunctions, communication errors, or software bugs. Implementing data validation, cleansing, and normalization techniques can help maintain data quality and consistency across IoT systems.
Data security and privacy
Integrating IoT data with other systems can introduce new security and privacy risks, as data may be exposed to unauthorized access or tampering during transmission or data storage. To mitigate these risks, developers should implement security best practices, such as encryption, authentication, and access control, to protect data throughout the integration process.
Scalability and performance
As IoT systems grow and generate increasing amounts of data, the ability to scale data integration processes becomes critical. Scalability challenges can arise from limitations in processing power, storage capacity, or network bandwidth. To address these challenges, developers can employ techniques such as data compression, caching, and parallel processing and leverage cloud-based data integration platforms that can scale on demand.
In summary, IoT data integration is an essential aspect of IoT systems, enabling organizations to combine IoT data with other sources to gain deeper insights and optimize their operations. Addressing challenges related to data format and protocol compatibility, data quality and consistency, data security and privacy, and scalability and performance is crucial for ensuring seamless and efficient data integration between IoT devices and other systems.
5.3. IoT Interoperability
Interoperability is a critical aspect of IoT systems, as it enables devices and components from different manufacturers and uses different communication protocols to work together seamlessly. Achieving interoperability in IoT systems can be challenging due to the diverse range of devices, protocols, and standards involved. However, it is essential for ensuring the efficient operation and management of IoT systems and facilitating the integration of new devices and technologies.
Standards and protocols
Standards and protocols play a crucial role in achieving interoperability in IoT systems. By adhering to established communication protocols, such as MQTT, CoAP, and Zigbee, IoT devices can communicate with each other and with other components in the IoT ecosystem, regardless of their manufacturer or underlying technology. Additionally, the use of standardized data formats, such as JSON or XML, can facilitate the exchange and processing of data between devices and systems.
Middleware and gateways
Middleware and gateways can also help address interoperability challenges in IoT systems. Middleware is software that acts as an intermediary between different devices and systems, enabling them to communicate and exchange data, even if they use different communication protocols or data formats. Gateways are hardware devices that perform a similar function, acting as a bridge between different networks or communication technologies. Both middleware and gateways can help ensure that IoT devices can communicate and interact with each other, regardless of their underlying technologies.
Application programming interfaces (APIs)
Application programming interfaces (APIs) are another important aspect of IoT interoperability. APIs provide a standardized way for devices and systems to interact with each other, enabling developers to build applications and services that can work with a wide range of IoT devices. By using well-defined APIs, developers can ensure that their applications can communicate with and control IoT devices, regardless of their specific implementation details.
In summary, IoT interoperability is essential for the efficient operation and management of IoT systems, as it enables devices and components from different manufacturers and using different communication protocols to work together seamlessly. Achieving interoperability in IoT systems involves the use of standards and protocols, middleware and gateways, and APIs, which together facilitate communication and interaction between diverse devices and systems.
Further Reading: HMI Technologies: The Ultimate Guide to Human-Machine Interface Innovations
Conclusion
Understanding the engineering aspects of IoT is crucial for the successful implementation and management of IoT systems. This article has explored various components of IoT systems, including architecture, protocols, security, device design and development, and system integration. By delving into these elements in detail, you can gain a deeper understanding of the technical foundations of IoT and how they contribute to the performance, reliability, and security of IoT deployments. As IoT continues to grow and evolve, staying informed about these engineering aspects will be essential for harnessing the full potential of IoT technology and addressing the challenges and opportunities it presents.
Frequently Asked Questions (FAQs)
Q: What are some common IoT communication protocols?
A: Some common IoT communication protocols include MQTT, CoAP, and Zigbee. Each protocol has its own set of advantages and trade-offs, making them suitable for different IoT applications and scenarios.
Q: How can IoT devices be secured?
A: IoT devices can be secured by implementing security best practices, such as device hardening, secure communication, data protection, and regular firmware and software updates. Adhering to established security standards and frameworks can also help ensure the privacy, integrity, and availability of IoT systems.
Q: What is the role of cloud computing and edge computing in IoT data processing and storage?
A: Cloud computing provides scalable and flexible storage and processing capabilities for IoT data, while edge computing enables data processing closer to the source, reducing latency and bandwidth requirements. The choice between cloud and edge computing depends on the specific requirements of the IoT application, such as latency, data rate, and real-time processing needs.
Q: What are some examples of IoT applications and services?
A: IoT applications and services can be found across various industries, such as smart homes, smartwatches, industrial IoT, agriculture, and smart cities. These applications leverage IoT data to optimize processes, improve efficiency, and enhance user experiences.
Q: Why is interoperability important in IoT systems?
A: Interoperability is essential for IoT systems because it enables devices and components from different manufacturers and uses different communication protocols to work together seamlessly. Achieving interoperability involves the use of standards and protocols, middleware and gateways, and APIs, which together facilitate communication and interaction between diverse devices and systems.
Q: What is the future of IoT?
There has been an exponential rise in the growth and development of IoT in terms of new devices and applications. It is expected to see further growth with the help of artificial intelligence and machine learning. This will create more revolution in various applications such as healthcare, wearables, automotive, smartphones, supply chains, customer experience, security systems, smart devices, etc.
Q: How is IoT used in data analytics?
Companies can drive innovation by leveraging the power of IoT and Data Analytics to unlock valuable insights and make data-driven decisions. By connecting various devices and sensors through the Internet of Things (IoT), companies can gather vast amounts of real-time data, creating opportunities for transformative change. This data, often referred to as big data, can be analyzed using advanced data analytics techniques to extract meaningful patterns, trends, and correlations.
Data analytics enables companies to uncover valuable insights that were previously hidden within vast volumes of data. Companies can gain a deeper understanding of their business models, customer behaviors, and market trends by applying statistical models, machine learning algorithms, and data visualization tools. This knowledge can fuel innovation and drive strategic decision-making.
References
-
Internet of Things for beginners – the complete guide [Internet]. Thingsquare. 2021 [cited 2023 Jul 14]. Available from: https://www.thingsquare.com/blog/articles/iot-for-beginners/
-
Nativapps. IoT (internet of things): A comprehensive guide to building smart and connected devices [Internet]. NativApps Inc. Nativapps; 2023 [cited 2023 Jul 14]. Available from: https://nativapps.com/en/iot-internet-of-things-a-comprehensive-guide-to-building-smart-and-connected-devices/
-
4 Yourself C. Become an IoT pro: A comprehensive guide to the internet of things | download C 4 yourself app now! [Internet]. Youtube; 2023 [cited 2023 Jul 14]. Available from: https://www.youtube.com/watch?v=A_VfUTlq084
-
Follow L. Introduction to internet of things (IoT) [Internet]. GeeksforGeeks. 2018 [cited 2023 Jul 14]. Available from: https://www.geeksforgeeks.org/introduction-to-internet-of-things-iot-set-1/
-
Leelajay Technologies. Internet over things (IoT): Ultimate guide to IoT for beginners [Internet]. Linkedin.com. 1680784879000 [cited 2023 Jul 14]. Available from: https://www.linkedin.com/pulse/internet-over-things-iot-ultimate-guide-beginners